OAuthVishing
ShinyHunters: Vishing-led OAuth abuse hits Salesforce; coordinated extortion and...
ShinyHunters represents one of the most prolific and sophisticated data exfiltration groups of the past five years, responsible for compromising over 1 billion user records across hundreds of organizations worldwide.
From their Pokemon-inspired origins in 2020 to their recent evolution into a decentralized extortion-as-a-service operation, this threat actor has fundamentally reshaped the cybercrime landscape through innovative social engineering tactics, strategic forum administration, and persistent adaptation to law enforcement pressure.
## Executive Summary
ShinyHunters emerged in May 2020 as a financially motivated cybercrime collective specializing in large-scale data theft and underground marketplace operations.
The group's name derives from Pokemon "shiny hunting" - the practice of seeking rare, alternate-colored Pokemon - reflecting their methodology of targeting valuable, "shiny" datasets from high-profile organizations.
Their operations span critical infrastructure across telecommunications, financial services, healthcare, retail, and technology sectors, with victims including Microsoft, Google, [AT\&T](https://www.secureblink.com/cyber-security-news/atandt-rebuffed-the-claims-of-databreach-following-the-auction-of-70-million-of-its-user-databases), [Ticketmaster](https://www.secureblink.com/cyber-security-news/massive-ticketmaster-data-breach-exposes-560-m-customers-sparks-lawsuit), and numerous Fortune 500 companies.
The group's significance extends beyond individual breaches to encompass broader cybercrime ecosystem management. ShinyHunters administrators have operated multiple iterations of [BreachForums](https://www.secureblink.com/cyber-security-news/breach-forums-shutdown-is-not-the-end-of-the-story-here-s-why), the internet's largest stolen data marketplace, facilitating thousands of cybercriminal transactions and serving as a critical hub for threat actor collaboration.
Recent law enforcement actions in France resulted in the arrest of four key members in June 2025, yet operations continue under a decentralized model that demonstrates remarkable organizational resilience.
Most concerning is the group's recent tactical evolution toward sophisticated social engineering campaigns targeting cloud infrastructure, particularly Salesforce environments through voice phishing (vishing) attacks.
These operations, conducted in collaboration with other elite threat actors like Scattered Spider, represent a paradigm shift from opportunistic data theft to targeted enterprise infiltration with significantly higher impact potential.
## Threat Actor Profile
### Origins and Formation
ShinyHunters first appeared on cybercrime forums in early May 2020, immediately distinguishing themselves through the scale and audacity of their initial operations.
Within two weeks of their debut, the group offered over 200 million user records for sale on dark web marketplaces, announcing their presence with breaches of major platforms including Tokopedia (91 million records) and Unacademy (22 million records). This explosive introduction established their reputation as a serious threat actor capable of compromising well-protected systems at unprecedented scale.
The group's moniker reflects both their methodology and cultural identity within gaming communities. [Pokemon](https://www.secureblink.com/cyber-security-news/pokemon-nft-card-game-site-used-to-distribute-net-support-rat) "shiny hunting" involves systematic, patient searching for rare variants - a parallel to their approach of methodically targeting high-value datasets from prominent organizations.
This cultural reference also served as operational security, allowing members to communicate using gaming terminology that provided natural cover for criminal activities.
### Organizational Structural Evolution
Initial intelligence suggested ShinyHunters operated as a small, tight-knit collective with specialized roles including reconnaissance, initial access, data exfiltration, and marketplace operations.
However, recent analysis indicates a more complex, decentralized structure resembling an extortion-as-a-service model where the "ShinyHunters" brand provides legitimacy and market access for multiple affiliated groups.
French law enforcement arrests in June 2025 targeted four core members identified by aliases "ShinyHunters," "Hollow," "Noct," and "Depressed," along with "IntelBroker" who was arrested separately in February 2025.
Despite these significant arrests, operations have continued under new leadership, suggesting either deeper organizational redundancy or successful transition to a franchise-based model where the brand operates independently of original founders.
### Business Model
ShinyHunters operates as a purely financially motivated threat actor with multiple revenue streams designed to maximize profit from stolen data. Their business model has evolved significantly since 2020, transitioning from simple data sales to sophisticated extortion operations that leverage both private negotiations and public pressure campaigns.
**Primary Revenue Streams:**
- **Direct Data Sales**: Initial operations focused on selling stolen databases on underground forums for prices ranging from \$500 to \$40,000 depending on data sensitivity and volume
- **Extortion Operations**: Evolution toward direct victim extortion with ransom demands ranging from \$200,000 (AT\&T) to \$8 million (Ticketmaster)
- **Forum Administration**: Revenue from BreachForums operations including vendor fees, premium memberships, and transaction commissions
- **Collaboration Services**: Acting as data brokers for other threat actors and providing initial access as a service
The group demonstrates sophisticated understanding of data monetization, often releasing samples publicly to establish authenticity while maintaining larger datasets for private sales or extortion. Their strategy of delayed extortion - sometimes waiting months between breach and ransom demands - maximizes leverage by allowing organizations to develop false confidence in their security posture.
## Chronological Timeline of Activity
### Stage 1: The Great Data Harvest (May 2020 - July 2021)
ShinyHunters' initial campaign, dubbed "Stage 1" by the group themselves, focused on mass data acquisition through opportunistic exploitation of vulnerable systems. This period established their reputation through high-profile breaches targeting popular consumer platforms and services.
**May 2020 - Initial Emergence:**
- **Tokopedia Breach**: 91 million user records from Indonesia's largest e-commerce platform, including names, emails, phone numbers, and hashed passwords.
- **Microsoft GitHub Incident**: Claimed theft of 500GB of source code from private Microsoft repositories, with 1GB released as proof
- **Unacademy Compromise**: 22 million records from Indian online education platform
**Mid-2020 Expansion:**
- **HomeChef**: 8 million meal kit delivery service customers
- **Zoosk**: 30 million dating app users
- **Chatbooks**: 15 million photo printing service customers
- **Mindful**: 2 million wellness platform users
- **Minted**: 5 million design marketplace users
**July 2020 - Stage 2 Escalation:**
- **Wattpad**: 270 million social storytelling platform users in their largest single breach to date
- **[BigBasket](https://www.secureblink.com/cyber-security-news/bigbasket-under-databreach-exposing-over-20million-for-free)**: 20 million Indian online grocery customers
- **AnimalJam**: 46 million records from children's gaming platform
### Stage 2: Consolidation and Forum Operations (2021-2023)
This period marked ShinyHunters' transition from purely operational activities to ecosystem management through forum administration and strategic partnerships. The group began focusing on higher-value targets while simultaneously building infrastructure for long-term cybercrime facilitation.
**2021 Operations:**
- **AT\&T Wireless**: 70 million subscriber records including personal information and Social Security numbers
- **Pixlr**: 1.9 million photo editing service users
- **Dave Inc**: 7.5 million digital banking customers
**BreachForums Administration (2023-2025):**
ShinyHunters assumed control of BreachForums following the arrest of original administrator "pompompurin" in March 2023. Under their leadership, the forum became the primary global marketplace for stolen data, facilitating thousands of transactions and serving as a coordination hub for international cybercrime operations.
### Stage 3: Advanced Persistent Extortion (2024-2025)
The current phase represents ShinyHunters' evolution into sophisticated, targeted operations combining traditional data theft with advanced social engineering and strategic extortion campaigns. This period is characterized by collaboration with other elite threat actors and focus on high-value cloud infrastructure.
**2024 Major Operations:**
- **[Ticketmaster](https://www.secureblink.com/cyber-security-news/569-gb-ticketmaster-breach-exposed-snowflake-data-resale)**: 560 million Live Nation customer records with ransom demands escalating from \$1 million to \$8 million
- **Advanced Persistent Presence**: Establishing long-term access to multiple systems for sustained data collection
**2025 Salesforce Campaign:**
The group's most sophisticated operation to date involves systematic targeting of Salesforce environments across multiple industries through coordinated vishing attacks. Confirmed victims include Google, Adidas, LVMH brands, [Allianz Life](https://www.secureblink.com/cyber-security-news/1-1-m-affected-in-allianz-life-data-breach-via-social-engineering), Air France-KLM, Pandora, [Qantas](https://www.secureblink.com/cyber-security-news/hacked-or-broken-qantas-airways-app-exposes-passenger-data-mid-flight), Chanel, and Farmers Insurance.
## Technical Analysis
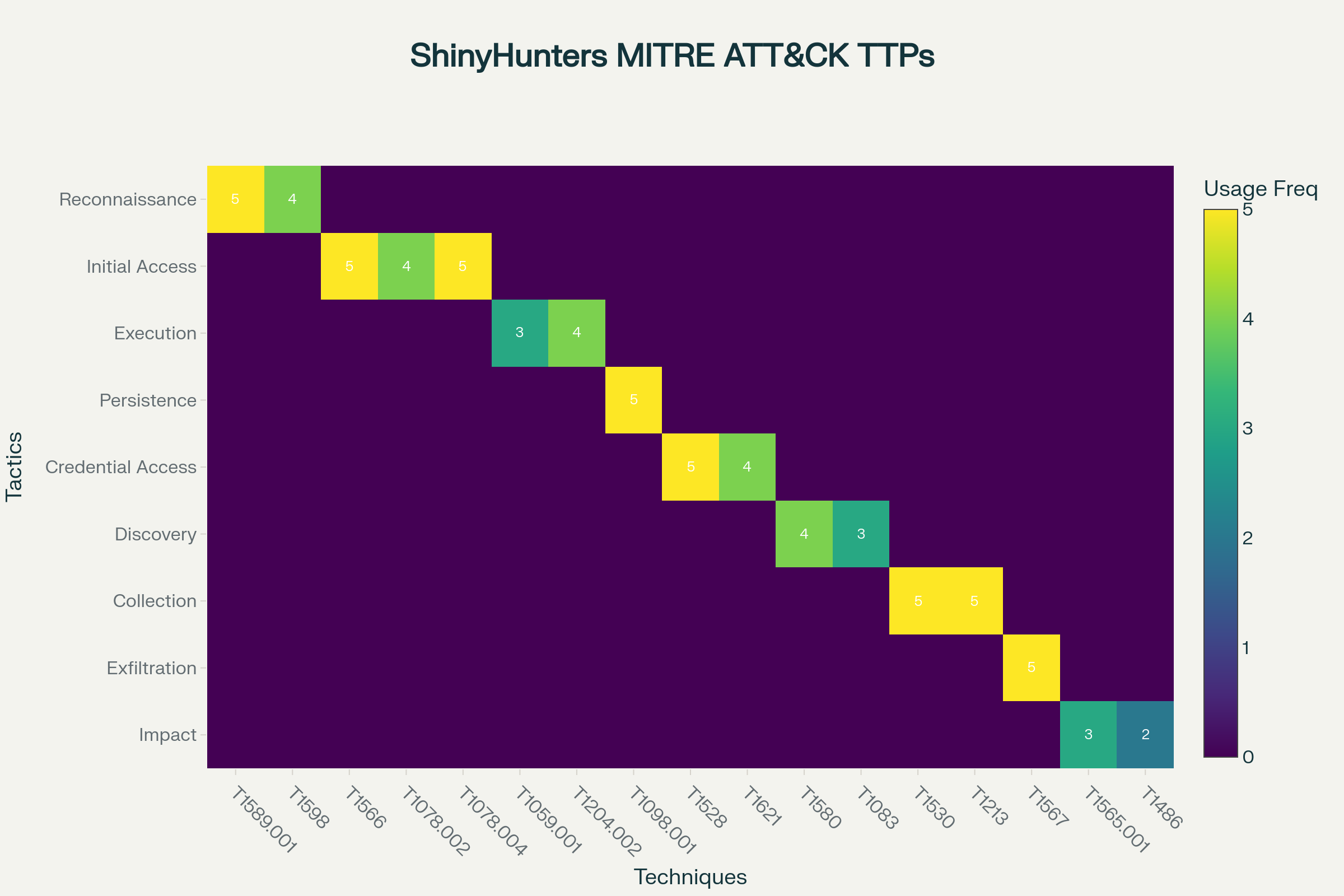
***ShinyHunters MITRE ATT\&CK Framework TTP Mapping***
### Tactics, Techniques, and Procedures (TTPs)
ShinyHunters demonstrates advanced technical capabilities across the full spectrum of cyber operations, with particular expertise in social engineering, cloud infrastructure exploitation, and data exfiltration at scale. Their methodology combines opportunistic vulnerability exploitation with targeted, intelligence-driven operations against high-value systems.
**Initial Access Methodologies:**
**Social Engineering Excellence**: The group's most distinctive capability lies in sophisticated social engineering operations that exploit human psychology rather than technical vulnerabilities.
Their vishing campaigns involve extensive reconnaissance to identify appropriate targets, development of convincing pretexts, and manipulation of organizational trust relationships to achieve access objectives.
Recent Salesforce campaigns demonstrate unprecedented sophistication in social engineering execution.
Attackers conduct detailed research on target organizations to identify appropriate personnel, develop convincing technical support scenarios, and guide victims through complex authentication processes while maintaining the illusion of legitimate IT assistance.
These operations often involve multiple contact attempts, escalation scenarios, and psychological pressure tactics designed to overcome natural security awareness.
**Credential Harvesting and Stuffing**: ShinyHunters employs multiple approaches to credential acquisition including targeted phishing campaigns, exploitation of previously breached databases, and automated credential stuffing attacks against high-value targets.
The group maintains extensive databases of compromised credentials from their own operations and third-party sources, enabling persistent access attempts across multiple platforms.
**GitHub Repository Analysis**: A significant component of their reconnaissance involves systematic analysis of target organization GitHub repositories to identify potential vulnerabilities, exposed credentials, and architectural information.
This approach allows identification of security weaknesses in application code, misconfigured authentication systems, and exposed API keys that can facilitate initial access.
**Execution and Persistence Techniques:**
**OAuth Application Abuse**: ShinyHunters has pioneered sophisticated abuse of OAuth authorization frameworks, particularly within Salesforce environments. Their methodology involves the creation of malicious connected applications disguised as legitimate business tools, social engineering of users to authorize these applications, and exploitation of granted permissions to maintain persistent access without triggering traditional authentication monitoring.
The technical execution involves registering OAuth applications with names like "My Ticket Portal" or "Salesforce Data Management Tool" that appear legitimate to end users. These applications request extensive permissions including data access, query capabilities, and administrative functions. Once authorized, the applications generate long-lived access tokens that enable ongoing data extraction without further user interaction or multi-factor authentication requirements.
**Custom Tool Development**: Technical analysis reveals sophisticated custom tooling designed specifically for large-scale data extraction and processing. These tools include modified versions of legitimate applications like Salesforce Data Loader, custom Python scripts for automated data harvesting, and specialized utilities for processing and formatting stolen datasets for marketplace sales.
**Infrastructure and Operational Security:**
**Traffic Obfuscation and Anonymization**: All operational activities employ multiple layers of traffic obfuscation including Tor networks, commercial VPN services (particularly Mullvad VPN), and proxy chains to complicate attribution and evade detection. This infrastructure enables sustained access to compromised systems while maintaining operational security against law enforcement and security researcher tracking.
**Distributed Command and Control**: Rather than traditional centralized C2 infrastructure, ShinyHunters operates through distributed communication channels including encrypted messaging platforms, underground forums, and ephemeral communication systems that provide resilience against law enforcement disruption.
### Data Exfiltration and Processing Capabilities
ShinyHunters demonstrates exceptional capabilities in large-scale data processing, with operations involving hundreds of millions of records requiring sophisticated technical infrastructure and methodology. Their approach combines automated collection systems with manual analysis to identify high-value datasets within broader data repositories.
Technical evidence suggests deployment of custom automated collection tools capable of systematically extracting data from various database systems, cloud storage platforms, and application programming interfaces. These systems employ parallel processing techniques to maximize collection speed while minimizing detection probability through distributed query patterns.
Stolen datasets undergo systematic processing to identify personally identifiable information, financial data, authentication credentials, and other high-value information categories. This processing enables strategic pricing and marketing of datasets based on data sensitivity and potential criminal utility.
The group employs sophisticated quality assurance processes to verify dataset authenticity and completeness before marketplace listing or extortion operations. This includes automated validation of data formats, manual spot-checking of records, and cross-referencing with known data sources to ensure accuracy and prevent fraudulent listings that could damage their reputation.
## Data Breaches and Cyberattacks
| Organization | Date | Records | Sector | Geography |
|-------------------------------------------|------------|---------------------|-------------------|----------------|
| Tokopedia | 2020-05-02 | 91 million | E-commerce | Indonesia |
| Microsoft GitHub | 2020-05-15 | 500GB source code | Technology | Global |
| Unacademy | 2020-05-20 | 22 million | Education | India |
| Wattpad | 2020-07-15 | 270 million | Social Media | Canada |
| BigBasket | 2020-10-01 | 20 million | E-commerce | India |
| Pixlr | 2021-01-15 | 1.9 million | Technology | Global |
| Dave Inc | 2021-07-01 | 7.5 million | Financial Services| United States |
| AT&T | 2021-08-01 | 70 million | Telecommunications| United States |
| Ticketmaster | 2024-05-29 | 560 million | Entertainment | Global |
| Adidas | 2025-05-01 | 5 million (est) | Retail/Fashion | Global |
| Pandora | 2025-06-01 | 2 million (est) | Jewelry/Retail | Global |
| Qantas | 2025-06-01 | 5 million (est) | Aviation | Australia |
| Chanel | 2025-06-01 | 3 million (est) | Luxury Goods | Global |
| Google | 2025-06-01 | 2.55 million | Technology | Global |
| LVMH (Louis Vuitton, Dior, Tiffany) | 2025-06-15 | 10 million (est) | Luxury Goods | Global |
| Air France-KLM | 2025-07-15 | 3 million (est) | Aviation | Europe |
| Allianz Life | 2025-07-01 | 1.4 million | Insurance | North America |
| Farmers Insurance | 2025-08-01 | 1.1 million | Insurance | United States |
| Workday | 2025-08-22 | Business contacts | HR Technology | Global |
### Comprehensive Victim Analysis
ShinyHunters' five-year operational history encompasses breaches across virtually every major industry sector, with particular concentration in technology, financial services, retail, and telecommunications. Their victim selection demonstrates strategic targeting of organizations with large customer databases, valuable intellectual property, or strategic importance within critical infrastructure sectors.
The group's most significant operations have targeted major technology companies including Microsoft, Google, and numerous software-as-a-service providers. These breaches often involve source code theft, customer database exfiltration, and compromise of development infrastructure that can enable supply chain attacks against downstream customers.
The Microsoft GitHub breach in May 2020 represented a watershed moment demonstrating the group's capability to compromise even the most security-conscious organizations. While Microsoft initially disputed the significance of the compromise, subsequent analysis confirmed the authenticity of stolen source code, establishing ShinyHunters' credibility within cybercrime communities and attracting significant law enforcement attention.
Recent operations demonstrate increasing focus on financial services organizations including digital banking platforms, insurance companies, and payment processors. These targets offer high-value personal financial information, transaction data, and authentication credentials that command premium prices on underground markets.
The compromise of Farmers Insurance affecting 1.1 million customers represents typical current operations combining technical sophistication with strategic targeting of organizations likely to pay substantial ransoms to prevent data publication. Similar patterns appear in attacks against Allianz Life and other insurance providers where regulatory compliance requirements create additional pressure for rapid incident resolution.
**Retail and Luxury Brands**: The 2025 Salesforce campaign particularly targeted luxury retail brands including LVMH companies (Louis Vuitton, Dior, Tiffany \& Co.), Adidas, Chanel, and Pandora. These organizations possess high-value customer databases containing wealthy individuals' personal information that serves both extortion and identity theft purposes.
Luxury brand targeting also serves psychological warfare purposes, as these organizations typically have strong brand protection concerns and may pay substantial ransoms to prevent reputational damage associated with customer data breaches. The group's public disclosure of compromised luxury brands generates significant media attention that increases pressure on other potential victims.
### Attack Methodology Evolution
ShinyHunters' operational methodology has undergone significant evolution from opportunistic vulnerability exploitation to highly targeted, intelligence-driven operations requiring substantial planning and resource investment. This evolution reflects both increased law enforcement pressure requiring improved operational security and recognition that targeted attacks against high-value organizations generate superior financial returns compared to mass exploitation of vulnerable systems.
**Early Opportunistic Phase (2020-2021)**: Initial operations focused on identifying and exploiting publicly accessible vulnerabilities, misconfigured systems, and exposed databases. This approach enabled rapid accumulation of large datasets but generated relatively modest financial returns due to commodity pricing for common personal information categories.
**Strategic Targeting Phase (2022-2024)**: Operations evolved toward research-driven targeting of specific organizations based on data value assessment, financial capability analysis, and security posture evaluation. This phase involved substantial pre-operation intelligence gathering including reconnaissance of target personnel, system architecture analysis, and development of organization-specific attack methodologies.
**Advanced Persistent Extortion Phase (2024-2025)**: Current operations represent highly sophisticated, multi-month campaigns involving persistent access maintenance, continuous data collection, and strategic extortion timing designed to maximize victim pressure and ransom payment probability.
These operations often involve collaboration with other elite threat actors and deployment of novel attack techniques specifically developed for high-value targets.
### Collaboration Networks and Partnerships
Recent intelligence indicates extensive collaboration between ShinyHunters and other prominent threat actors, particularly Scattered Spider and LAPSUS$, forming what researchers term "[Scattered LAPSUS$ Hunters](https://www.secureblink.com/cyber-security-news/lapsus-hackers-elevate-sim-swapping-attacks-to-unprecedented-heights)". These partnerships enable more sophisticated operations through shared resources, specialized expertise, and distributed operational capabilities that complicate law enforcement attribution and disruption efforts.
**Scattered Spider Partnership**: This collaboration combines ShinyHunters' data exfiltration expertise with Scattered Spider's advanced social engineering capabilities and initial access techniques.
Joint operations typically involve Scattered Spider gaining initial network access through sophisticated vishing campaigns, followed by ShinyHunters conducting large-scale data extraction and subsequent extortion operations.
**LAPSUS\$ Affiliation**: Evidence suggests ongoing relationships with LAPSUS\$ members providing additional technical capabilities, particularly in areas of cloud infrastructure exploitation and multi-factor authentication bypass.
This relationship has enabled operations against previously inaccessible high-security environments including government systems and critical infrastructure organizations.
**Forum Ecosystem Management**: Beyond operational partnerships, ShinyHunters' administration of BreachForums creates extensive networks with hundreds of other cybercriminals including initial access brokers, malware developers, and specialized service providers.
This ecosystem provides substantial intelligence, resource sharing, and collaboration opportunities that enhance their operational capabilities significantly beyond their core team's direct expertise.
## Business Model
ShinyHunters operates as a sophisticated criminal enterprise with diversified revenue streams, strategic market positioning, and long-term business planning that distinguishes them from opportunistic cybercriminal groups.
Their approach combines traditional data theft with modern extortion techniques, marketplace operations, and service provision to other criminals in a comprehensive business model designed for sustained profitability and growth.
### Financial Operations and Revenue Optimization
**Tiered Pricing Strategy**: The group employs sophisticated pricing models based on data sensitivity, victim organization profile, and market demand dynamics.
Basic personal information databases typically sell for \$500-\$3,500, while specialized datasets containing financial information, healthcare records, or corporate intelligence command significantly higher prices reaching \$40,000 or more for premium datasets.
Recent evolution toward direct extortion has dramatically increased revenue potential, with ransom demands ranging from \$200,000 for smaller organizations to \$8 million for major corporations like Ticketmaster.
This shift reflects recognition that organizations will pay substantially more to prevent data publication than criminals will pay to acquire published datasets.
**Strategic Market Timing**: ShinyHunters demonstrates sophisticated understanding of market dynamics, often timing data releases and extortion demands to maximize psychological pressure on victims. This includes coordinating releases with major news cycles, regulatory compliance deadlines, or competitive business activities that increase organizational sensitivity to reputation damage.
The group's practice of delayed extortion - maintaining access for months before making demands - serves multiple strategic purposes including comprehensive data collection, victim organization assessment, and timing optimization for maximum leverage. This patience distinguishes them from opportunistic criminals focused on immediate monetization.
### Ecosystem Development, Infrastructure Investment
**BreachForums Administration**: Operation of the internet's largest stolen data marketplace represents a significant long-term investment in cybercrime ecosystem development. Forum administration provides multiple revenue streams including vendor fees, premium memberships, transaction commissions, and strategic intelligence about emerging threats and opportunities.
Forum control also enables market manipulation through selective promotion of certain data types, strategic timing of major releases, and coordination with other criminal organizations to maximize overall ecosystem profitability. This level of market influence provides substantial competitive advantages in their core data theft operations.
**Service Provider Evolution**: Recent evidence indicates evolution toward providing specialized services to other criminal organizations including initial access brokerage, data processing and validation, and extortion negotiation services.
This diversification reduces dependence on direct operations while leveraging their expertise and reputation to generate consistent revenue from the broader criminal ecosystem.
### Risk Management and Operational Resilience
**Decentralized Operations**: Following law enforcement arrests in France, ShinyHunters has adapted through operational decentralization that maintains brand recognition while reducing individual member exposure.
This model enables continued operations despite personnel losses and provides resilience against future law enforcement actions.
**Brand Value Protection**: The group invests substantially in reputation management within criminal communities, including consistent delivery on promises, quality assurance for data sales, and reliable service provision to other criminals. This reputation represents significant business value that enables premium pricing and preferential partnerships within the criminal ecosystem.
**Strategic Intelligence**: ShinyHunters maintains extensive intelligence capabilities focused on law enforcement activities, security researcher tracking, and competitive threat assessment.
This intelligence enables proactive operational security adjustments, strategic timing of major operations, and early warning systems for potential disruption attempts.
## Strategic Implications for Organizations
The evolution of ShinyHunters from opportunistic data thieves to sophisticated enterprise-targeting threat actors represents a fundamental shift in the cybercrime landscape with far-reaching implications for organizational security strategies, regulatory compliance frameworks, and industry-wide risk management approaches.
Their success has inspired numerous imitators and established operational methodologies that are being adopted by threat actors globally, creating a multiplier effect that extends their impact far beyond their direct operations.
### Industry-Specific Risk Assessment
**Technology Sector Vulnerabilities**: ShinyHunters' focus on technology companies reflects both the high value of intellectual property and customer data held by these organizations and their often-complex security environments that create exploitation opportunities.
Software-as-a-service providers face particular risk due to their role as data processors for multiple client organizations, creating single points of failure that can impact thousands of downstream customers simultaneously.
The group's systematic exploitation of cloud infrastructure, particularly Salesforce environments, demonstrates sophisticated understanding of modern enterprise architecture and the trust relationships that enable business operations.
Organizations heavily dependent on cloud services must reassess their security models to account for social engineering attacks that bypass technical controls through human manipulation.
**Financial Services Exposure**: The increasing focus on financial services organizations reflects both the direct value of financial data and the regulatory pressure these organizations face that makes them more likely to pay substantial ransoms. Insurance companies face particular vulnerability due to their possession of detailed personal information combined with regulatory requirements that create time pressure for incident response.
Digital banking platforms and fintech companies represent especially attractive targets due to their technology-forward approaches that may lack the mature security controls of traditional financial institutions while processing substantial financial transactions and maintaining extensive customer databases.
**Critical Infrastructure Implications**: While ShinyHunters has not directly targeted critical infrastructure systems, their collaboration with other threat actors and proven ability to compromise high-security environments creates potential for operations against power grids, telecommunications networks, and transportation systems. The group's advanced social engineering capabilities could potentially be applied to compromise industrial control systems through manipulation of operational personnel.
### Regulatory and Compliance Challenges
**Cross-Border Enforcement Limitations**: ShinyHunters' international operations across multiple jurisdictions create substantial challenges for law enforcement agencies and regulatory bodies attempting to coordinate response efforts. The group's use of distributed infrastructure, encrypted communications, and jurisdictional shopping complicates traditional law enforcement approaches and creates safe havens for continued operations.
Organizations must develop compliance strategies that account for the reality that law enforcement may be unable to provide meaningful protection against sophisticated international threat actors, requiring increased reliance on technical controls and proactive security measures rather than deterrence through legal consequences.
**Data Protection Regulation Evolution**: The group's sophisticated data monetization strategies highlight gaps in current data protection regulations that focus primarily on breach notification rather than prevention of criminal data monetization. Organizations face increasing regulatory pressure to implement comprehensive data protection measures that address not only traditional privacy concerns but also criminal exploitation of personal information.
The evolution of extortion-based attacks creates new regulatory challenges around ransom payment policies, with organizations facing difficult decisions between immediate financial costs and long-term reputational and regulatory consequences of data publication.
### Economic Impact Market Effects
**Insurance Market Disruption**: The scale and sophistication of ShinyHunters operations, combined with their high success rate in obtaining ransom payments, is contributing to significant changes in cybersecurity insurance markets. Insurance providers are implementing more stringent security requirements, increasing premiums substantially, and in some cases refusing coverage for organizations deemed high-risk.
The group's focus on high-value targets with substantial insurance coverage creates an adversarial dynamic where successful attacks against well-insured organizations provide both immediate ransom revenue and market intelligence about insurance policy limits that inform future targeting decisions.
**Competitive Intelligence Risks**: ShinyHunters' systematic collection of corporate data creates opportunities for competitive intelligence theft that extends beyond traditional concerns about customer data protection. Organizations must consider the strategic implications of intellectual property, business strategy documents, and competitive information falling into criminal hands where it may be sold to competitors or hostile nation-states.
**Supply Chain Security**: The group's targeting of technology service providers creates cascading risks throughout supply chains as compromised providers may enable access to their client organizations. This creates complex risk management challenges where organizations must assess not only their direct security posture but also the security capabilities of all critical service providers and the potential for lateral compromise through trusted relationships.
## Detection and Mitigation Guidance
Effective defense against ShinyHunters requires comprehensive security strategies that address both their technical capabilities and sophisticated social engineering techniques. Traditional perimeter-focused security models prove insufficient against threat actors who primarily exploit human vulnerabilities and legitimate system features rather than deploying malicious software or exploiting technical vulnerabilities.
### Technical Detection Strategies
**OAuth Application Monitoring**: Organizations must implement comprehensive monitoring of OAuth application creation, modification, and usage patterns to detect malicious applications before they can be exploited for data exfiltration. This includes automated analysis of permission requests, unusual application naming patterns, and usage anomalies that may indicate unauthorized access.
Detection systems should flag OAuth applications requesting excessive permissions, applications created outside normal business processes, and applications exhibiting unusual data access patterns characteristic of bulk data extraction operations. Real-time monitoring of application authorization events can enable rapid response to social engineering attempts before attackers obtain persistent access.
**Behavioral Analytics for Cloud Environments**: ShinyHunters' sophisticated use of legitimate credentials and authorized applications requires behavioral analytics systems capable of detecting subtle anomalies in user activity patterns. These systems must establish baselines for normal data access patterns and identify deviations that may indicate unauthorized access by external parties using compromised credentials.
Specific indicators include unusual query patterns, bulk data exports outside normal business hours, access from unexpected geographic locations or network segments, and data access patterns inconsistent with user role requirements. Integration of multiple data sources including authentication logs, application usage telemetry, and network traffic analysis provides comprehensive visibility into potential compromise indicators.
**Network Traffic Analysis**: The group's consistent use of VPN services and Tor networks for operational security creates opportunities for network-based detection through analysis of traffic patterns and destination analysis. Organizations should implement monitoring for connections to known VPN providers, Tor exit nodes, and other anonymization services during sensitive data access operations.
Deep packet inspection and network behavior analysis can identify data exfiltration attempts through monitoring of outbound data flows, particularly large file transfers or database query results being transmitted to external destinations. This analysis must account for legitimate business use of privacy tools while maintaining sensitivity to potential malicious usage patterns.
### Human-Centered Defense Strategies
**Advanced Social Engineering Training**: Traditional security awareness training proves insufficient against ShinyHunters' sophisticated social engineering techniques that exploit human psychology and organizational trust relationships. Organizations require specialized training programs that simulate the specific tactics used by advanced threat actors, including vishing scenarios, impersonation techniques, and pressure tactics designed to bypass natural security instincts.
Training programs must include realistic simulation exercises where employees experience high-pressure scenarios similar to those employed by ShinyHunters, including impersonation of IT support personnel, urgent business scenarios requiring immediate action, and technical instructions that appear legitimate but enable unauthorized access. Regular testing and reinforcement ensure training effectiveness against evolving social engineering techniques.
**Verification and Callback Procedures**: Organizations must implement mandatory verification procedures for any requests involving system access, data handling, or security configuration changes, regardless of the apparent authority or urgency of the request. These procedures should include independent verification through established communication channels, multi-person authorization for sensitive operations, and documentation requirements that create audit trails for security-relevant activities.
Callback procedures should require verification of identity through independently obtained contact information rather than information provided by the requestor, multi-step verification processes that include questions only legitimate personnel would know, and escalation procedures for unusual or high-risk requests.
**Organizational Trust Management**: ShinyHunters' success relies heavily on exploitation of organizational trust relationships, requiring systematic review and hardening of trust assumptions within business processes. This includes analysis of who has authority to request various actions, what verification requirements exist for different types of requests, and how emergency procedures may be exploited to bypass normal security controls.
Organizations should implement zero-trust principles for human interactions similar to network security models, requiring verification and authentication for all significant requests regardless of apparent source authority. This cultural shift requires executive leadership support and comprehensive change management to avoid creating operational friction that encourages workaround behaviors.
### Systemic Security Architecture
**Identity and Access Management Hardening**: Defense against OAuth abuse and credential-based attacks requires comprehensive identity and access management systems with strong authentication requirements, granular permission controls, and continuous monitoring capabilities. Multi-factor authentication must be mandatory for all administrative functions and configured to resist social engineering attempts that manipulate users into approving illegitimate authentication requests.
Privileged access management systems should implement just-in-time access provisioning, time-limited permissions for sensitive operations, and automatic revocation of unused access rights. Regular access reviews and automated analysis of permission usage patterns can identify both over-privileged accounts and unusual access patterns that may indicate compromise.
**Data Loss Prevention and Encryption**: Comprehensive data loss prevention systems must account for authorized users extracting data through legitimate applications, requiring content-aware monitoring that can identify sensitive data regardless of the extraction method. These systems should implement automatic classification of sensitive data, monitoring of data movement patterns, and real-time blocking of unauthorized data transfers.
Encryption strategies must address both data at rest and data in motion, with particular attention to ensuring that encrypted data cannot be accessed by unauthorized applications even when users possess legitimate system credentials. Key management systems must prevent credential compromise from enabling widespread data decryption.
**Incident Response and Recovery**: Organizations must develop incident response procedures specifically designed for sophisticated social engineering attacks where traditional indicators of compromise may be absent. These procedures should include rapid OAuth application review processes, emergency access revocation capabilities, and comprehensive forensic analysis that can identify the full scope of data access even when attackers use legitimate credentials and applications.
Recovery procedures must address both immediate containment of ongoing access and long-term remediation of compromised trust relationships, potentially requiring complete rebuilding of authentication systems and re-evaluation of all access permissions. Organizations should maintain offline backup systems that cannot be accessed through normal network credentials to ensure recovery capabilities even in cases of comprehensive credential compromise.
## Future Outlook
The trajectory of ShinyHunters' operations indicates continued evolution toward increasingly sophisticated, targeted attacks that blend advanced technical capabilities with masterful social engineering to compromise even the most security-conscious organizations.
Their successful adaptation to law enforcement pressure through organizational decentralization and operational innovation suggests sustained threat levels despite periodic disruptions, while their collaboration networks and influence within cybercrime ecosystems amplify their impact far beyond direct operations.
### Tactical Evolution Predictions
**Enhanced Artificial Intelligence Integration**: Future operations will likely incorporate artificial intelligence technologies to improve social engineering effectiveness, automate reconnaissance activities, and optimize data processing and monetization strategies.
AI-powered voice synthesis and conversation management could enable more convincing vishing campaigns with reduced human resource requirements, while machine learning algorithms could automate identification of high-value data within compromised systems.
Natural language processing capabilities may enable automated analysis of corporate communications to identify optimal extortion timing, key decision-makers, and pressure points that maximize ransom payment probability. These technologies could also enable personalized social engineering campaigns tailored to specific individuals based on comprehensive analysis of their digital footprints and behavioral patterns.
**Supply Chain and Third-Party Integration Attacks**: The group's demonstrated expertise in exploiting trust relationships suggests future focus on supply chain attacks that leverage compromised service providers to access multiple downstream targets simultaneously. Software-as-a-service providers, managed security service providers, and other trusted third parties represent high-value targets that provide access to hundreds or thousands of client organizations through single successful compromises.
These attacks may involve long-term persistent access to service provider systems followed by strategic deployment against specific high-value clients, creating complex attribution challenges and enabling coordinated attacks against entire industry sectors.
**Advanced Persistent Extortion Models**: Current trends toward delayed extortion and comprehensive data collection suggest evolution toward more sophisticated extortion models that maintain access for extended periods while continuously collecting intelligence about victim organizations. Future operations may involve systematic collection of competitive intelligence, regulatory compliance documentation, and internal communications that provide multiple leverage points for extortion demands.
This approach could enable tiered extortion strategies where initial ransom demands focus on data publication prevention, followed by additional demands related to competitive intelligence, regulatory violation evidence, or other compromising information collected during extended access periods.
### Industry and Geographic Expansion
**Critical Infrastructure Targeting**: The group's increasing sophistication and collaboration with nation-state-affiliated actors create potential for operations against critical infrastructure systems including power grids, telecommunications networks, and transportation systems. These targets offer both substantial ransom potential and strategic value for nation-states seeking to demonstrate capabilities or conduct preparatory operations for future conflicts.
Critical infrastructure attacks may involve extended reconnaissance periods, development of specialized attack tools, and coordination with other threat actors possessing complementary capabilities such as industrial control system expertise or insider access. The intersection of financial motivation with strategic objectives creates complex threat scenarios that challenge traditional defensive assumptions.
**Emerging Market Focus**: Geographic analysis suggests potential expansion into emerging markets where cybersecurity capabilities may be less mature while economic development creates attractive targets with substantial data holdings. Financial services organizations, telecommunications providers, and government agencies in developing regions may face particular risk due to rapid digitization combined with limited security expertise and infrastructure.
These markets may also offer operational advantages including less sophisticated law enforcement capabilities, limited international cooperation mechanisms, and regulatory environments that provide additional leverage for extortion operations.
**Regulatory Arbitrage Operations**: The group's demonstrated ability to operate across multiple jurisdictions suggests potential development of regulatory arbitrage strategies that exploit differences in cybercrime laws, data protection regulations, and law enforcement capabilities between countries.
Operations may be specifically designed to maximize complications for law enforcement while exploiting regulatory pressure on victim organizations.
This could include targeting organizations subject to strict data protection regulations with operations conducted from jurisdictions with limited cybercrime enforcement, creating maximum pressure for rapid ransom payment to avoid regulatory penalties.
### Ecosystem Impact and Influence
**Methodology Proliferation**: ShinyHunters' successful techniques are already being adopted by numerous other threat actors, creating a multiplication effect that extends their impact throughout the cybercrime ecosystem. Their social engineering playbooks, OAuth abuse techniques, and extortion strategies provide templates for less sophisticated criminals to conduct similar operations against smaller targets.
This proliferation effect creates industry-wide risk elevation as defensive measures must account not only for ShinyHunters' direct operations but also for dozens of imitator groups employing similar techniques with varying levels of sophistication. The democratization of advanced attack techniques through criminal forums and collaboration networks accelerates this proliferation process.
**Criminal Infrastructure Development**: The group's extensive forum administration and ecosystem management activities suggest continued development of criminal infrastructure that enables and amplifies threat actor capabilities globally. Future developments may include specialized service markets, automated attack platforms, and comprehensive support ecosystems that lower barriers to entry for cybercriminal operations.
This infrastructure development creates positive feedback loops where successful operations generate resources that fund development of more sophisticated capabilities, creating exponential growth in overall ecosystem threat levels. The intersection of profit motivation with infrastructure investment suggests sustained growth in criminal capabilities that outpaces defensive development.
**Law Enforcement Adaptation Challenges**: The group's successful adaptation to law enforcement pressure through organizational decentralization and operational innovation suggests that traditional law enforcement approaches may prove insufficient against sophisticated, international cybercrime organizations.
Future operations may be specifically designed to exploit limitations in international cooperation, jurisdictional boundaries, and legal frameworks that constrain law enforcement effectiveness.
This evolution toward law enforcement-resistant operational models may inspire other threat actors to adopt similar approaches, creating systemic challenges for cybercrime enforcement that require fundamental changes in international cooperation mechanisms and legal frameworks.
The success of decentralized criminal organizations challenges traditional assumptions about law enforcement deterrence and creates demand for innovative protective strategies that do not rely primarily on legal consequences.
## Appendices
### Indicators of Compromise (IOCs)
**Network Indicators:**
- Email addresses: [email protected], contact-shinycorp-tutanota-com@[redacted]
- Malicious domains: dashboard-salesforce[.]com, login-salesforce[.]com, my-ticket-portal[.]com
- VPN/Tor traffic patterns: 185.220.101.0/24 (Tor exits), 193.138.218.0/24 (Mullvad VPN)
**Application Indicators:**
- OAuth application names: "My Ticket Portal", "Salesforce Data Management Tool", "CRM Analytics Dashboard"
- Suspicious user agents: Custom Salesforce Data Loader variants, modified Python requests libraries
- Bulk data export patterns: Large SOQL queries, automated database crawling behaviors
**Behavioral Indicators:**
- Vishing campaigns targeting IT personnel with Salesforce-related scenarios
- OAuth application authorization requests during business hours following IT contact
- Data access patterns inconsistent with normal user behavior profiles
- Network connections to anonymization services during data access operations
### Detection Rules and Signatures
**YARA Rules:**
```
rule ShinyHunters_Salesforce_Loader {
meta:
description = "Detects malicious Salesforce Data Loader variants"
author = "Threat Intelligence Team"
date = "2025-09-04"
strings:
$oauth_abuse = "oauth/device/authorize"
$bulk_export = "bulk/data/export"
$custom_agent = "ShinyLoader"
condition:
2 of them
}
```
**Sigma Rules:**
```yaml
title: Suspicious OAuth Application Creation
logsource:
product: salesforce
service: audit
detection:
selection:
action: "OAuth App Created"
permissions: "Full Access"
condition: selection
```**Network Detection:**
- Monitor for OAuth device authorization flows initiated outside normal business processes
- Detect bulk data export operations exceeding baseline thresholds
- Identify connections to known VPN/Tor infrastructure during data access events
- Alert on user agent strings inconsistent with standard Salesforce integrations
This comprehensive Threat Research of ShinyHunters demonstrates the evolution of cybercrime from opportunistic attacks to sophisticated, persistent threat operations that challenge traditional security assumptions and require fundamental changes in organizational defense strategies.
Their continued operations despite significant law enforcement pressure highlight the importance of proactive, technically sophisticated defensive measures that address both human and technical vulnerabilities in modern enterprise environments.






